Persona - Based on Email Address
Learn how to interpret email addresses and attempt to discover the real author associated
with an email.

Persona - Based on Email Address |
 |
| Shortcuts: Other related pages: Email Architecture Details, Whois, Traceroute, privacy, |
| Sources of Email |
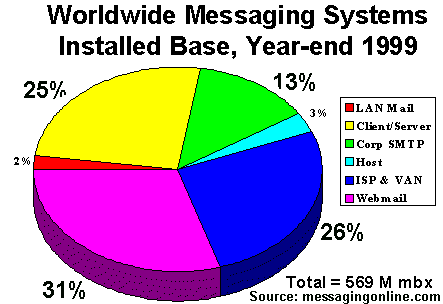
This pie chart shows where email accounts are hosted (source = messagingonline.com). 26% of accounts are associated with a user's Internet service provider (ISPs may be paid service or a free ISP) About 43% of email is through an employer/employee environment. This leaves a very large 31% of email accessed through web-based interfaces which tend to be free and fairly anonymous (Hotmail and yahoo dominate this market sector). Before you continue with the rest of this page, make sure you are familiar with the concepts of Email Architecture Details,
| Read the Whole email name |
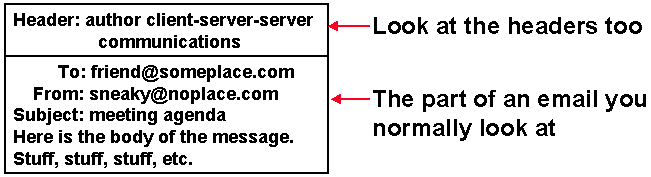
The "from" part of an email is absolutely unreliable. The user can put anything he wants there in their email client. To really understand where an email came from , you must look at the "headers" Headers contain additional information like where did your email server receive the message from, etc. It turns out that trying to track down the true source of an email is exactly what anti-spam advocates also work on. Therefore the best methods for identifying email can be gained from studying anti-spam techniques.
Most email servers will be properly configured to only send email from their own users. This way if the user is "mis-behaving" (sending spam, etc) than the system administrator can cancel the user's account. Unfortunately, some mail servers are configured to allow anybody to forward their email through the mail server. This is called an "open SMTP relay" and can be heavily exploited by spammers. Such sources of Spam are often identified on the RBL - Real-time Blackhole List - which is used by some ISPs to block Spam sources. Here is the RBL Home page, which also supports a query to see if a server is currently on the RBL.
For more information:
So far this web page has talked only about email addresses... But what about the user IDs people supply when using many forms of peer to peer applications? (AOL Instant Messenger, chat, powwow, IRC, Netmeeting, etc). Many of these applications will allow users to connect to each other based on a user-supplied ID which is often an email address. You should recognize that a user can provide ANY email address they want into the application. This will work just fine as long as your "buddies" know which email address you are using at that moment.
![[Russ Banner (9kb)]](russbanner.gif )
Note for my Alumni: Your referrals are always appreciated
| I can be reached at Russweb 'at' navigators.com or 703 -729-1757 Copyright Information Navigators |
|